Multi-Party Computation
Multi-Party Computation (MPC) powers MetaMask Embedded Wallets' non-custodial key management, enabling secure access and signing without exposing a full private key.
Understanding MPC in MetaMask Embedded Wallets
MetaMask Embedded Wallets utilizes threshold cryptography, a principle of MPC, to ensure that a user can access their private key or generate transaction signatures only if they meet a specified threshold - typically 2 out of n key shares.
Design goals
- Seamless user experience: MetaMask Embedded Wallets aims to provide a frictionless non-custodial wallet experience.
- Broad compatibility: Ensures integration with existing authentication methods and blockchain ecosystems.
- Global performance & scalability: Designed to meet the expansive demands of the Web3 market efficiently.
2-of-3 setup
- Authentication share: Derived from the user’s chosen login method (for example, social login such as Google).
- Device share: Stored on-device, protected by OS security/biometrics.
- Backup/2FA share: User-controlled recovery using a high-entropy secret.
Implementation variants
- Shamir Secret Sharing (SSS): Reconstructs the key when the threshold is met.
- Threshold Signature Scheme (TSS): Creates partial signatures; no key reconstruction.
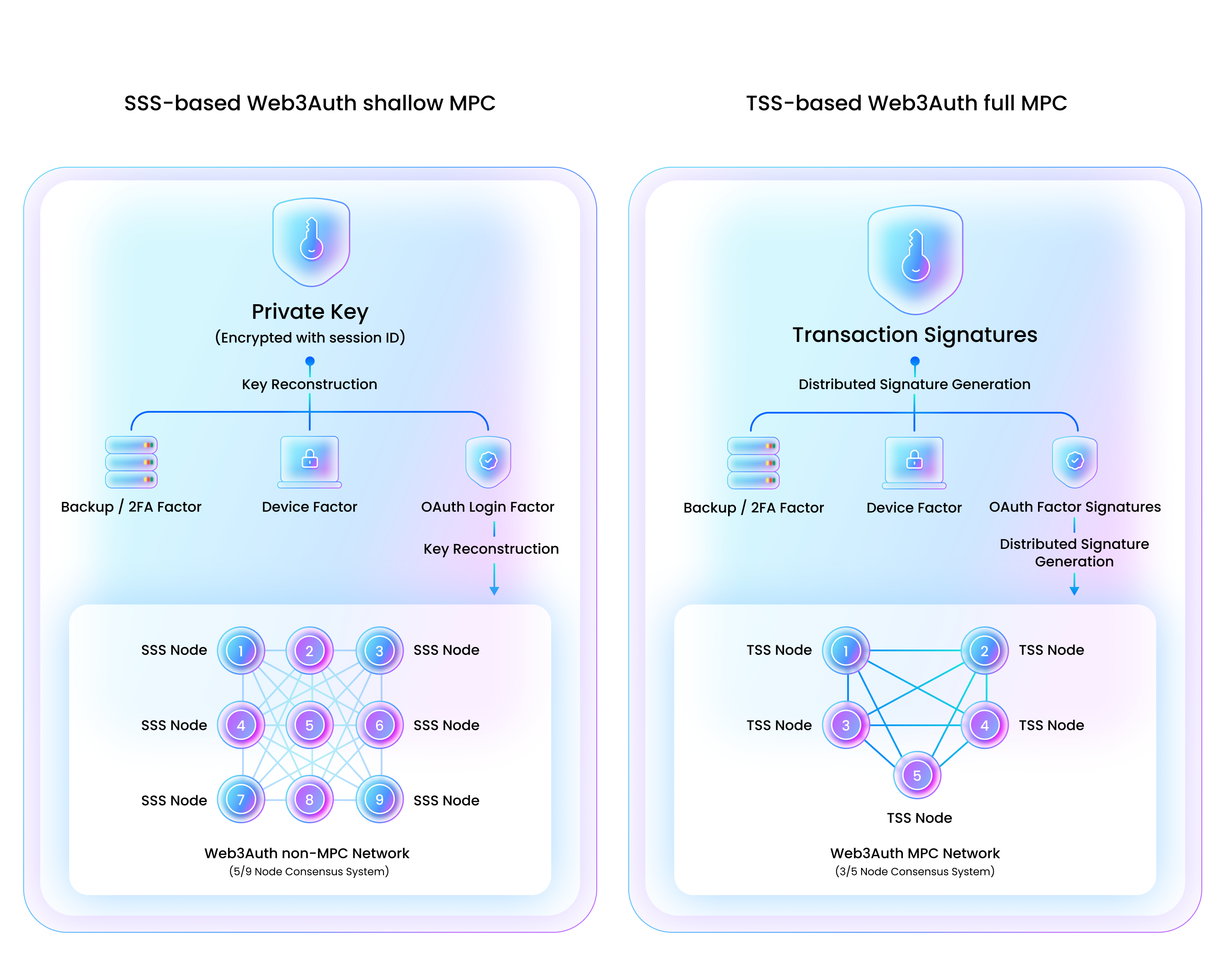
Both methods adhere to the core concept of threshold-based security but differ in their approach to wallet management and signature generation.
Wallet management infrastructure
The wallet management infrastructure distributes key shares so the full private key is never stored or exposed. The authentication share is generated by the Embedded Wallets Network using a 5/9 consensus, keeping wallets non-custodial.
Next steps
This section is an overview of MPC in MetaMask Embedded Wallets. For a more in-depth understanding, see: